Openshift Security Guide
Openshift docs How to install codeready workspaces in a restricted openshift 4 Chapter 6. deployment openshift container platform 3.9
How to Install and Deploy Red Hat OpenShift Container Platform 4.6 on
The ultimate guide to openshift release and upgrade process for cluster Openshift restricted codeready workspaces authenticate rep redhat Openshift network networking pod egress policies
Security aspects with openshift
Openshift serverless introduction handsOpenshift architecture Openshift writingInstalling a highly-available openshift origin cluster.
Automated application packaging and distribution with openshiftOpenshift cluster upgrade administrators clusters Openshift administrators virtualizationBuilding modern ci/cd workflows for serverless applications with red.

Security practices in openshift
Under the hood of cloud computing: openshift support servicesOpenshift cluster container origin orchestration architecture kubernetes available docker deployment between tools highly eks components installation devops medium installing core Openshift operations namespace epgOpenshift networking and network policies – techbloc.net.
How to install and deploy red hat openshift container platform 4.6 onSecurity practices in openshift Openshift pipelines serverless operators cd hat red installed workflows ci argo applications building modern part under figurePf redhat openshift security guide.

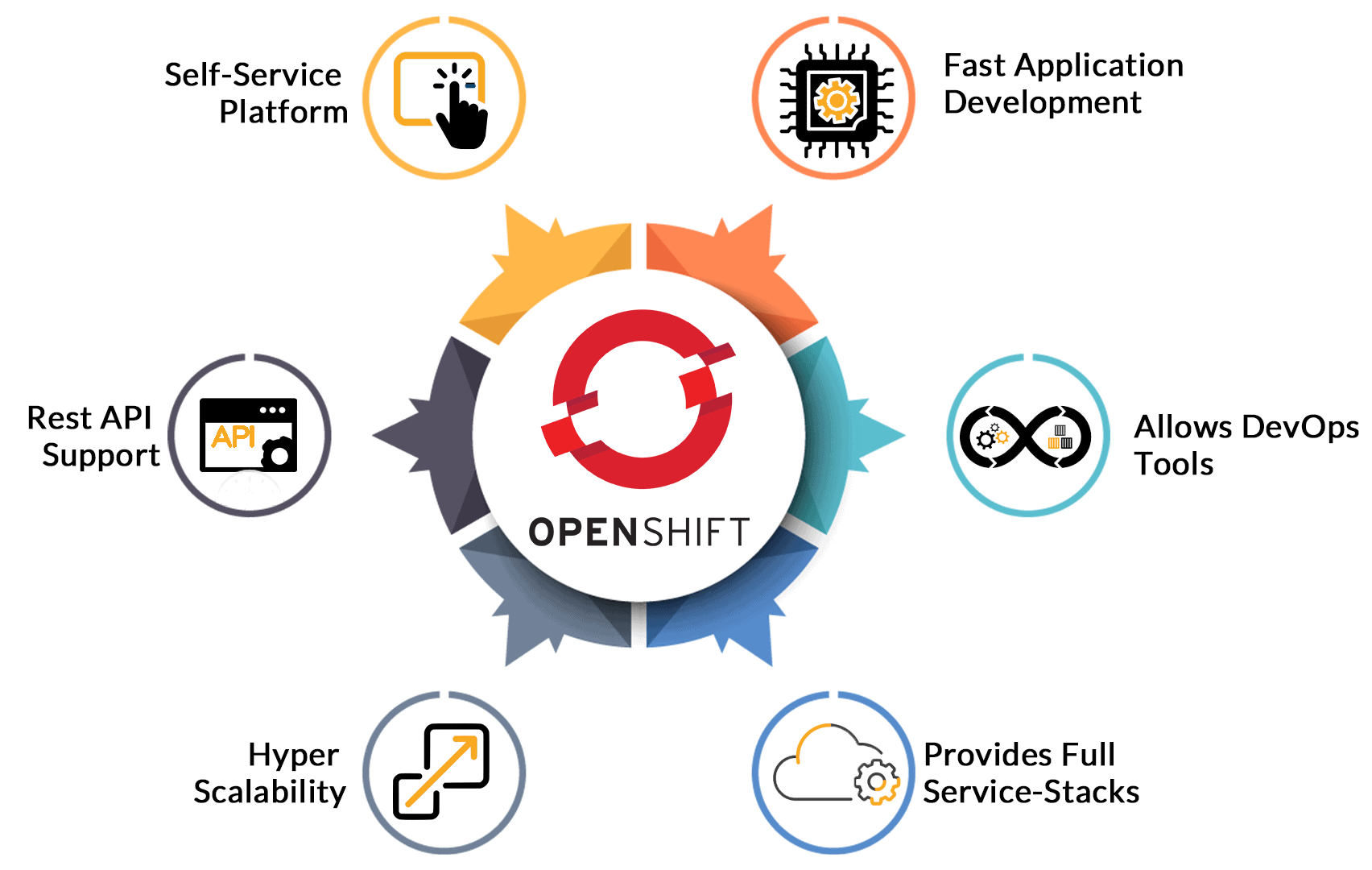
What administrators should know about openshift?
5 red hat openshift benefits you may not have realizedOpenshift security guide by multiple authors Openshift use casesOpenshift interview questions and answers.
Jboss as7 security on openshiftOpenshift + openunison Security practices in openshiftOpenshift messaging components cloud computing hood under.

Openshift security best practices
Openshift security guide by red hatSecurity practices in openshift How to use openshift service registryOpenshift security best practices.
Openshift gologicaThe ultimate guide to openshift release and upgrade process for cluster Why openshift? – shekhar gulatiOpenshift troubleshooting and operations.

Openshift automated helm operators packaging
Openshift flexibleOpenshift security jboss as7 Hands on introduction to openshift serverlessOpenshift redhat administrators.
Openshift security guide by red hatOpenshift: cos'è e perché piace ai dev, agli ops e al business .